Cyber Privacy 2024: The Evolution of Digital Privacy in the Swole Doge vs. Cheems Meme
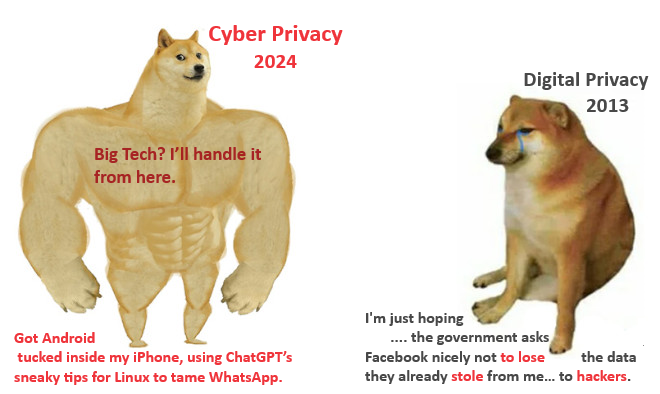
Is digital privacy evolving? Just ask Swole Doge and Cheems—two meme icons who hilariously capture the shift from passive data protection to taking the reins in the digital world.
At CyberPrivacyProtecTech, we believe that digital privacy has evolved far beyond its traditional boundaries. As we navigated the complexities of cybersecurity, we realized the need to coin and clarify the definition of a term that is rapidly gaining traction: Cyber Privacy. This concept is more than just an extension of digital privacy; it represents a fundamental shift in how individuals and organizations approach the protection of personal data in the modern, interconnected world.
To illustrate this shift, we created a visual representation using the popular "Swole Doge vs. Cheems" meme. This meme humorously and powerfully depicts the contrast between Digital Privacy 2013 and Cyber Privacy 2024.
1. Cheems (Digital Privacy 2013):
The Cheems side of the meme represents Digital Privacy 2013 with the phrase, "I'm just hoping the government asks Facebook nicely not to lose the data they already stole from me… to hackers." This phrase reflects the more passive approach to privacy that was prevalent during that time—a time marked by the first major Facebook data breach in 2013, where users were largely dependent on Big Tech and governments to safeguard their data. Users were essentially hoping for the best, without the tools or knowledge to take control of their own privacy.
2. Swole Doge (Cyber Privacy 2024):
In stark contrast, the Swole Doge embodies Cyber Privacy 2024. This side of the meme illustrates a shift toward a more empowered and proactive stance on privacy. The phrase, "Got Android tucked inside my iPhone, using ChatGPT’s sneaky tips to tame WhatsApp. Big Tech? I’ll handle it from here," showcases the advanced strategies modern users employ to secure their data.
- "Got Android tucked inside my iPhone" – This phrase is a metaphor for using containers and virtual environments to isolate and secure applications—essentially going to extreme lengths to protect digital life. This tactic aligns with our Containerization and Virtualization services, which allow users to safeguard their data by creating isolated environments where they can run applications securely.
- "Using ChatGPT’s sneaky tips to tame WhatsApp" – This highlights the modern user’s ability to leverage advanced AI-driven tools, like ChatGPT, to outsmart invasive applications. This reflects the services we offer, such as App Security Audits and Smartphone Privacy Consulting, which empower users to take control of their digital privacy through cutting-edge technology.
- "Big Tech? I’ll handle it from here" – This phrase encapsulates the essence of Cyber Privacy—users are no longer waiting for Big Tech to protect their data. Instead, they are rightfully taking matters into their own hands. This proactive approach, which we atCyberPrivacyProtecTech advocate, can be likened to a "cowboy shooting from the knee" stance—direct, effective, and unafraid to confront the challenges head-on. In essence, Cyber Privacy is about empowerment and the ability to defend one’s digital environment without relying on external entities.
3. Defining Cyber Privacy
As we seek to define Cyber Privacy, we view it as "digital privacy on steroids." It’s not merely a defensive posture but a bold, assertive approach to data protection, where trust is earned through constant verification and where real-time protection is paramount. Our services, grounded in the Zero Trust model, embody this philosophy by ensuring that every access request is scrutinized, and no entity is trusted by default.
Conclusion
In creating this meme, we wanted to convey more than just a comparison—we sought to capture the essence of the transformation from a passive to an active stance on digital privacy. Cyber Privacy represents the future of data protection, where users are no longer passive recipients but active defenders of their digital sovereignty. At CyberPrivacyProtecTech, we are at the forefront of this shift, providing the tools, knowledge, and expertise to empower our clients in the ever-evolving digital landscape.
This approach not only defines Cyber Privacy but also underscores the importance of taking control of your digital life in an increasingly interconnected world. As we say, Big Tech? We’ll handle it from here.